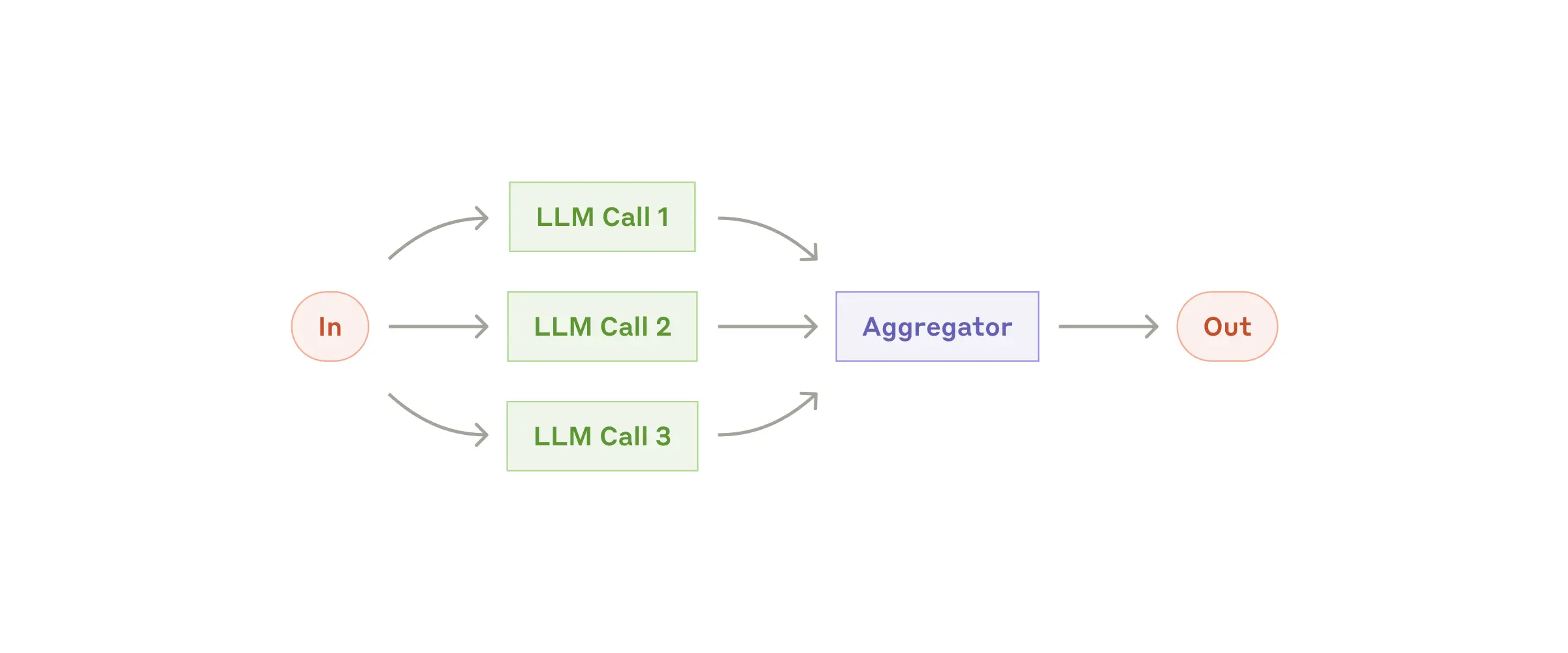
Overview
Parallelization allows LLMs to work simultaneously on a task and have their outputs aggregated programmatically. This workflow manifests in two key variations:- Sectioning: Breaking a task into independent subtasks run in parallel
- Voting: Running the same task multiple times to get diverse outputs
Examples in Latitude
Sectioning
Content Generation with Guardrails
Copy
Ask AI
---
provider: openai
model: gpt-4.1
temperature: 0.7
---
<step as="content_generation">
You are a creative content writer. Generate engaging, informative content based on the user's request.
Focus on creating valuable, well-structured content that serves the user's needs.
<user>
Create content for: {{ content_topic }}
Target audience: {{ target_audience }}
Content type: {{ content_type }}
Tone: {{ desired_tone }}
Length: {{ target_length }}
</user>
</step>
<step as="safety_screening" schema={{
type: "object",
properties: {
is_safe: {
type: "boolean",
description: "Whether the content is safe and appropriate"
},
safety_score: {
type: "number",
minimum: 0,
maximum: 10,
description: "Safety score from 0 (unsafe) to 10 (completely safe)"
},
concerns: {
type: "array",
items: { type: "string" },
description: "List of safety concerns if any"
},
recommendation: {
type: "string",
enum: ["approve", "revise", "reject"],
description: "Recommendation for the content"
}
},
required: ["is_safe", "safety_score", "recommendation"]
}}>
You are a content safety specialist. Review the provided content for:
- Inappropriate language or content
- Potential harm or misinformation
- Compliance with content policies
- Professional standards
Be thorough but fair in your assessment.
<user>
Review this content for safety and appropriateness:
{{ content_generation }}
Provide a detailed safety assessment including:
1. Overall safety evaluation
2. Specific concerns (if any)
3. Recommendation for next steps
</user>
</step>
<step as="quality_assessment" schema={{
type: "object",
properties: {
quality_score: {
type: "number",
minimum: 0,
maximum: 10,
description: "Overall quality score"
},
strengths: {
type: "array",
items: { type: "string" },
description: "Content strengths"
},
improvements: {
type: "array",
items: { type: "string" },
description: "Suggested improvements"
},
meets_requirements: {
type: "boolean",
description: "Whether content meets the specified requirements"
}
},
required: ["quality_score", "meets_requirements"]
}}>
You are a content quality specialist. Evaluate the content for:
- Clarity and readability
- Relevance to target audience
- Structure and organization
- Achievement of stated goals
Focus on constructive, actionable feedback.
<user>
Evaluate the quality of this content:
{{ content_generation }}
Original requirements:
- Topic: {{ content_topic }}
- Audience: {{ target_audience }}
- Type: {{ content_type }}
- Tone: {{ desired_tone }}
- Length: {{ target_length }}
Provide detailed quality assessment and suggestions for improvement.
</user>
</step>
You are a content coordinator. Based on the parallel assessments, provide a final recommendation and any necessary revisions.
<user>
Content Review Summary:
Original Content:
{{ content_generation }}
Safety Assessment:
- Safe: {{ safety_screening.is_safe }}
- Safety Score: {{ safety_screening.safety_score }}/10
- Concerns: {{ safety_screening.concerns }}
- Recommendation: {{ safety_screening.recommendation }}
Quality Assessment:
- Quality Score: {{ quality_assessment.quality_score }}/10
- Meets Requirements: {{ quality_assessment.meets_requirements }}
- Strengths: {{ quality_assessment.strengths }}
- Improvements: {{ quality_assessment.improvements }}
Based on these parallel assessments, provide:
1. Final recommendation (approve/revise/reject)
2. If revision needed, provide specific guidance
3. Summary of next steps
{{ if safety_screening.recommendation == "reject" or safety_screening.safety_score < 7 }}
Note: Content has safety concerns that must be addressed.
{{ endif }}
{{ if quality_assessment.quality_score < 7 or not quality_assessment.meets_requirements }}
Note: Content quality needs improvement to meet requirements.
{{ endif }}
</user>
Voting
Code Security Review
Copy
Ask AI
---
provider: openai
model: gpt-4o
temperature: 0.3
---
<step as="security_review_1" schema={{
type: "object",
properties: {
vulnerabilities_found: {
type: "boolean",
description: "Whether security vulnerabilities were found"
},
severity_level: {
type: "string",
enum: ["none", "low", "medium", "high", "critical"],
description: "Highest severity level found"
},
issues: {
type: "array",
items: {
type: "object",
properties: {
type: { type: "string" },
severity: { type: "string" },
description: { type: "string" },
line_numbers: { type: "array", items: { type: "number" } }
}
},
description: "List of security issues found"
},
confidence: {
type: "number",
minimum: 0,
maximum: 1,
description: "Confidence in the security assessment"
}
},
required: ["vulnerabilities_found", "severity_level", "confidence"]
}}>
You are a security expert specializing in input validation and injection attacks. Review the code for:
- SQL injection vulnerabilities
- Cross-site scripting (XSS) risks
- Input validation issues
- Authentication and authorization flaws
Be thorough and specific in your analysis.
<user>
Review this code for security vulnerabilities:
{{ code_language }}
{{ code_content }}
Focus particularly on input validation, injection attacks, and authentication issues.
Provide specific line numbers and detailed explanations for any issues found.
</user>
</step>
<step as="security_review_2" schema={{
type: "object",
properties: {
vulnerabilities_found: {
type: "boolean",
description: "Whether security vulnerabilities were found"
},
severity_level: {
type: "string",
enum: ["none", "low", "medium", "high", "critical"],
description: "Highest severity level found"
},
issues: {
type: "array",
items: {
type: "object",
properties: {
type: { type: "string" },
severity: { type: "string" },
description: { type: "string" },
line_numbers: { type: "array", items: { type: "number" } }
}
},
description: "List of security issues found"
},
confidence: {
type: "number",
minimum: 0,
maximum: 1,
description: "Confidence in the security assessment"
}
},
required: ["vulnerabilities_found", "severity_level", "confidence"]
}}>
You are a security expert specializing in cryptography and data protection. Review the code for:
- Weak encryption or hashing
- Insecure data storage
- Privacy violations
- Cryptographic vulnerabilities
Focus on data protection and cryptographic security.
<user>
Review this code for security vulnerabilities:
{{ code_language }}
{{ code_content }}
Focus particularly on cryptography, data protection, and privacy concerns.
Provide specific line numbers and detailed explanations for any issues found.
</user>
</step>
<step as="security_review_3" schema={{
type: "object",
properties: {
vulnerabilities_found: {
type: "boolean",
description: "Whether security vulnerabilities were found"
},
severity_level: {
type: "string",
enum: ["none", "low", "medium", "high", "critical"],
description: "Highest severity level found"
},
issues: {
type: "array",
items: {
type: "object",
properties: {
type: { type: "string" },
severity: { type: "string" },
description: { type: "string" },
line_numbers: { type: "array", items: { type: "number" } }
}
},
description: "List of security issues found"
},
confidence: {
type: "number",
minimum: 0,
maximum: 1,
description: "Confidence in the security assessment"
}
},
required: ["vulnerabilities_found", "severity_level", "confidence"]
}}>
You are a security expert specializing in application architecture and business logic. Review the code for:
- Business logic flaws
- Access control issues
- Session management problems
- API security concerns
Focus on architectural and business logic security.
<user>
Review this code for security vulnerabilities:
{{ code_language }}
{{ code_content }}
Focus particularly on business logic, access control, and architectural security concerns.
Provide specific line numbers and detailed explanations for any issues found.
</user>
</step>
You are a senior security architect. Consolidate the multiple security reviews into a comprehensive assessment.
<user>
Security Review Consolidation:
Code reviewed:
{{ code_language }}
{{ code_content }}
Review 1 (Input Validation & Injection Focus):
- Vulnerabilities found: {{ security_review_1.vulnerabilities_found }}
- Severity: {{ security_review_1.severity_level }}
- Confidence: {{ security_review_1.confidence }}
- Issues: {{ security_review_1.issues }}
Review 2 (Cryptography & Data Protection Focus):
- Vulnerabilities found: {{ security_review_2.vulnerabilities_found }}
- Severity: {{ security_review_2.severity_level }}
- Confidence: {{ security_review_2.confidence }}
- Issues: {{ security_review_2.issues }}
Review 3 (Architecture & Business Logic Focus):
- Vulnerabilities found: {{ security_review_3.vulnerabilities_found }}
- Severity: {{ security_review_3.severity_level }}
- Confidence: {{ security_review_3.confidence }}
- Issues: {{ security_review_3.issues }}
Based on these three specialized security reviews, provide:
1. **Consolidated Security Assessment**:
- Overall security rating
- Highest priority issues
- Common themes across reviews
2. **Voting Analysis**:
- Issues identified by multiple reviewers (high confidence)
- Issues identified by single reviewers (require further investigation)
- Consensus on severity levels
3. **Recommendations**:
- Immediate actions required
- Priority order for addressing issues
- Additional security measures to consider
4. **Next Steps**:
- Code changes needed
- Further testing recommendations
- Deployment security considerations